Disping was hacked and how I found other vulnerabilities
Posted by on
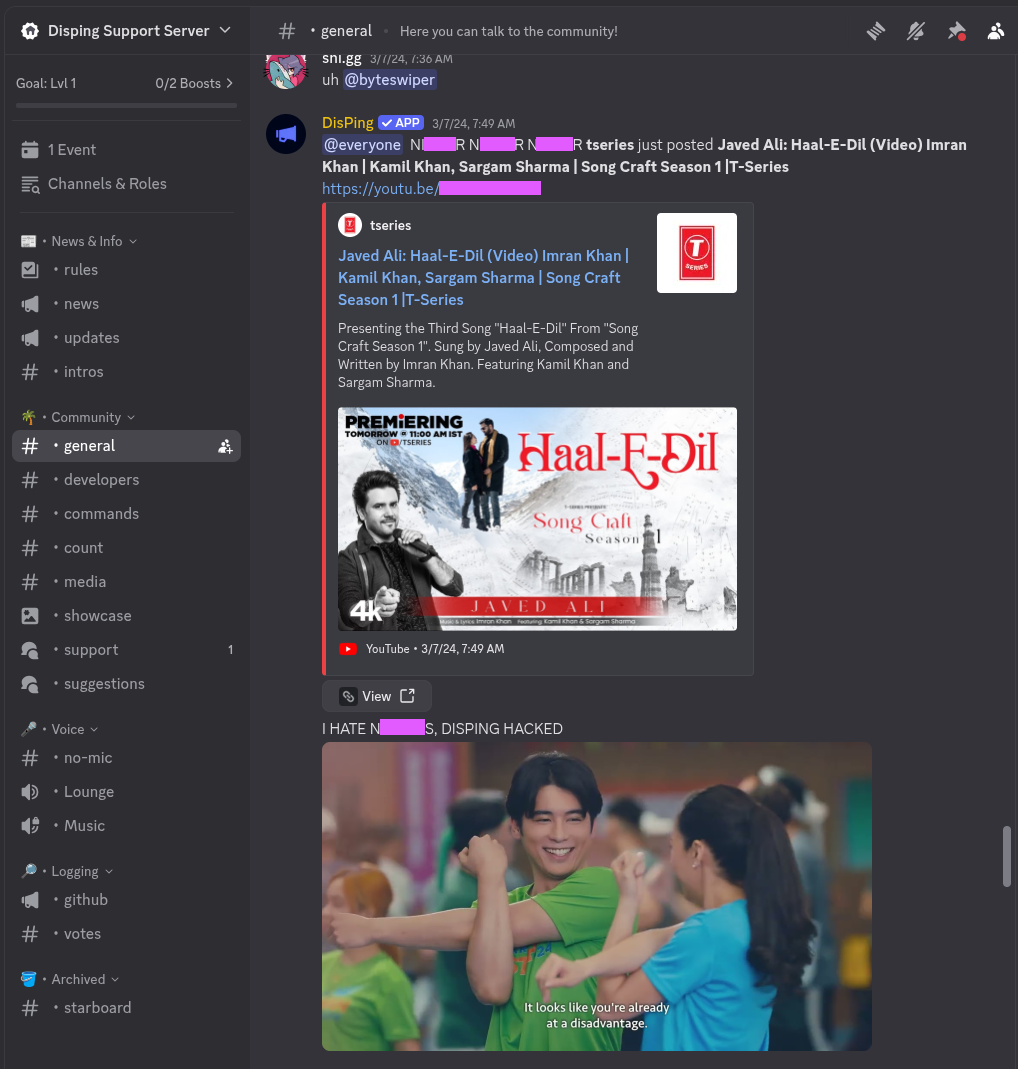
I used to be active on the community server of the DisPing Discord Notification Bot. On Tuesday the 7th of March 2024, I found a security vulnerability that allowed attackers to create and setup nonsensical notifications in various servers, potentially pinging users, using racial slurs and more as DisPing. This was the second time this has happened. This was made possible by an unauthenticated database endpoint.
 source
source
This made me want to take a closer look at the DisPing api. The bot had a single endpoint to manage guilds on the dashboard, 'api.disping.xyz/database', which did not check permissions when modifying or creating data.
A spoofed request to the api could look like this:
curl https://api.disping.xyz/database \ -X POST \ -H "Content-Type: application/json" \ -H "authorization: abc" \ -d '{"message":"TEST why doesnt this work,","username":"discord","channel":"1063636139606560778","advanced":{"embed_enabled":true,"embed_author":true,"embed_description":true,"embed_thumbnail":true,"embed_timestamp":true,"embed_button":true,"color":"red"},"type":"CREATE","social":"youtube","gid":"763803059876397056","uid":"821472922140803112"}'
This is a sample curl request to execute the attack. They and I were able to modify the 'gid' (discord guild id) field in the JSON body. The api never did any validation whatsoever on whether the claimed 'uid' had access to modify the claimed 'gid', all that was only checked on 'GET' requests, but never on 'POST'. The only things that had to match were the 'authorization' header and the 'uid' JSON body field. The developer of DisPing, Jake, confirmed that this request 'spoofing' was used for the spam in the DisPing support server and others.
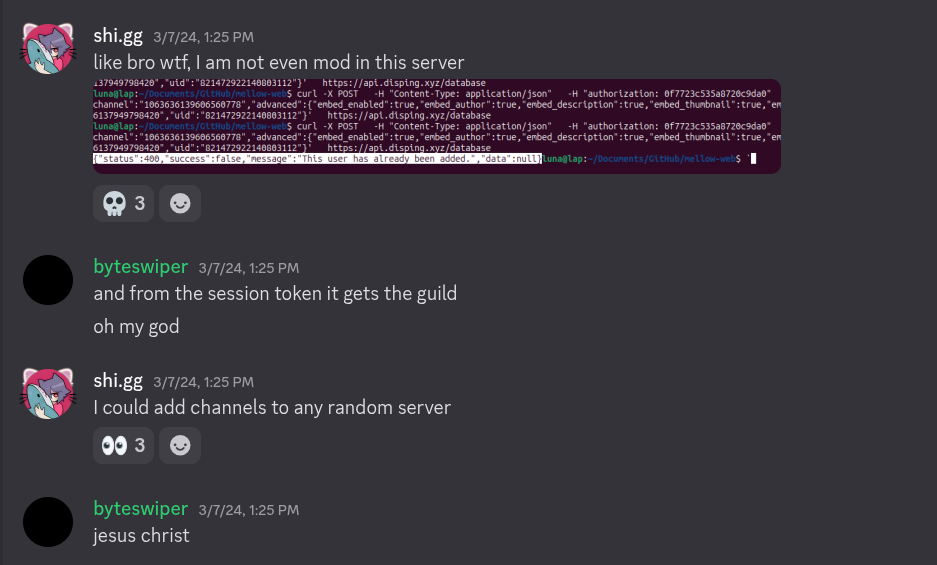 source
source
This vulnerability was not even found within a day of the dashboard's release. I reported it directly to the developer and it was fixed the same day.
Previous incident
Regarding the previous incident on 7 April 2023, where DisPing started spamming crypto scams and leaving servers massively. The history of DisPing leaving many servers can be found on topstats.gg .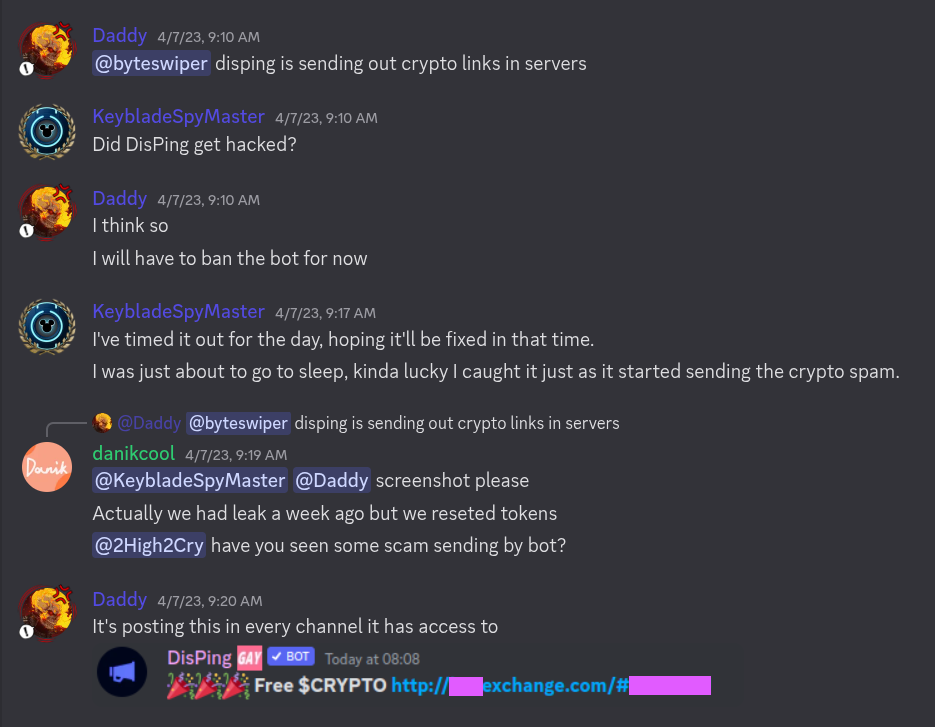 source
source
What the exact vulnerability was is not publicly known. I would guess that the bot token was somehow compromised, as the issue was resolved immediately after the active bot token was reset.
Opinion
What I personally think is important to learn here, is that developers should put a lot more effort and testing into their api routes, and double check if they validate all the fields, permissions and etc correctly. Personally, I'd recommend testing apis on a weekly basis and also have it tested by other independent security researchers.Author of the Article